Intended audience
If you want to understand what CSRF is, and the impact it could have on your organisation, continue reading this article. This article was written for both business stakeholders and technical professionals.
We assume that you have at least a basic understanding of how websites work, more specifically, the request-response model.
There are 4 dedicated sections, depending on your interest and skill level:
Example of a typical CSRF attack
Lets start with a very basic example of what a typical CSRF attack looks like. From OWASP, we have the following definition:
Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they’re currently authenticated.
In the example below, we have a malicious user that tricks a legitimate user into clicking a link. This link will send a request (from the victim’s machine), to a website that they are currently logged into.
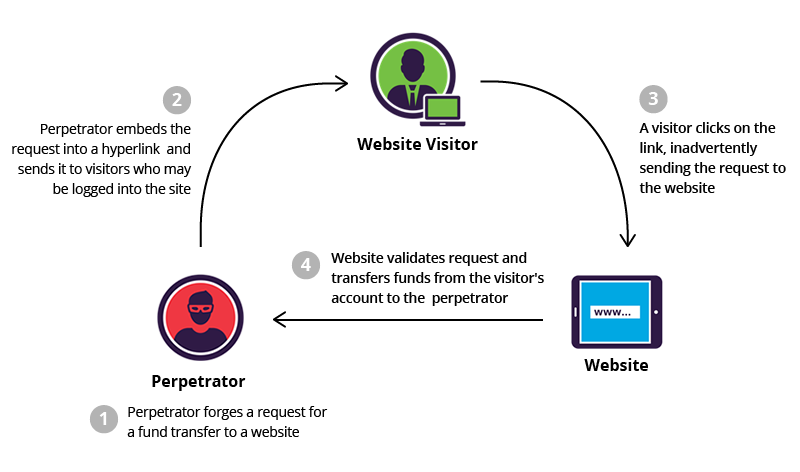
Seeing that the request originates from the victim’s computer, it looks like a legitimate request from the user to the web server, and this server will happily try and process the request on behalf of the user.
In the example above, the attacker uses a hyperlink and is attempting to transfer money from a victim’s account using social engineering techniques. This is just one of many ways the CSRF vulnerability can be exploited, but the basic idea stays the same: trick a user into doing something unintentional, that benefits the attacker.
We will cover more advanced techniques & attack vectors in an upcoming section, but first, let’s zoom out a bit and take a look at the business implications CSRF can have on an organisation.
Business Impacts of CSRF
The successful exploitation of a CSRF attack could have far-reaching implications for any organisation. Some of the most common business risks include:
- Financial loss / Reputational damage
- Unauthorised data access / Fraudulent modifications
- Employee impersonation / Communication breaches
- Data Loss / Operational Downtime
- Compliance, governance and regulations
Lets explore each one of these business risks in more detail, and see how they have an impact on business value.
Financial loss / Reputational damage
One of the most important business implications, is the financial impact that a cyber attack can have on an organisation. Things that can negatively impact business profits include, for example:
- Physical assets (servers) that needs to be replaced
- Operational downtime, meaning missed revenue
- Loss of customers, due to reputational damage
- Fines and legal implications for non-compliance
Business value comes in many forms, not just financial. For example, reputational damage could lead to a loss of customers confidence, and cause business churn or lower sales revenue.
Unauthorised data access / Fraudulent modifications
Seeing that this technique leverages ways to trick the user into doing something they did not intend to do, there is a real threat of a malicious threat actor getting access to sensitive data, or even worse, fraudulently modifying that data.
As illustrated in the example above, this could be in the form of a fraudulent money transfer, but could also be more subtle. For example, changing the user’s banking details, email address, or other means of extracting value from a user.
Auditing and tracking these fraudulent transactions could also be difficult, seeing that the victim user’s fingerprints are on the transaction, not the malicious user’s.
There is also a real risk of data exfiltration, meaning sensitive data is stolen and copied outside of the organisation’s control.
Employee impersonation / Communication breaches
If the target victim is an employee of the company, unauthorised data access and modification can become an even bigger risk.
For example, if an attacker can successfully change a user’s login details, or email address, to something the attacker controls, they can essentially take over that user’s account.
A more subtle risk would be if the malicious user can intercept confidential communications. This could allow the attacker access to sensitive (internal) communications. They could use this to their benefit (eg: insider trading, leaking or selling IP).
If the user (victim) is authorised to make statements on behalf of the company, this could also be used to communicate wrong or misleading information to your customers and investors, once again contributing to reputational damage.
Data Loss / Operational Downtime
In some use cases, CSRF vulnerabilities could also lead to data loss or data corruption.
From a business perspective, this is important, as it could lead to operational downtime, or even worse, missing transactional records needed for accounting purposes.
A good disaster recovery plan can help mitigate this risk, but even with a fully up-to-date and backed up database, there is still the risk that the CSRF vulnerability is present in your backup.
The implication being, even on a freshly installed new system, the vulnerability could still potentially be hiding in your data. This could give the attacker the ability to regain access and control.
Compliance, governance and regulations
This point is often overlooked, but companies and organisations have to comply with certain rules and regulations. This varies from industry to industry, and country to country.
As an example, if you process credit card transactions, then PCI DSS (Payment Card Industry Data Security Standard) comes into play. Unauthorised access to a customer’s credit card details, is punishable with a fine or even a class action lawsuit.
In Europe, another common one would be GDPR compliance, where organisations are responsible for safeguarding personal information about EU citizens, punishable with a fine.
For the health industry (especially in the US), there is also HIPPA (Health Insurance Portability and Accountability Act). Failure to comply can lead to huge fines.
Typically, fines are set as a percentage of total yearly revenue, meaning it could have a huge impact on your company’s profit margins.
Technical Impacts of CSRF
We already covered the business risks associated with CSRF’s, but let’s now go a bit deeper. Let’s see the technical impacts such an vulnerability can have on your IT system.
- Risks - We will first look at the most common risks to IT systems and infrastructure
- Attack Vectors - Then cover some common methods that are used in the wild for exploitation
- Indicators of Compromise - Then look at common tactics, techniques and procedures (TTP’s)
Technical risks associated with CSRF
We have two perspectives to consider:
From an IT systems perspective a successful CSRF attack is essentially hijacking a valid (and authenticated) victim’s user account, to do something bad.
From a threat actors point of view, changing user data or state would be low hanging fruit, if unprotected. For example, changing user profile & billing options (eg: email address, password, banking details).
This could also be used to force user purchases or other transactions without the users consent. For example, subscribing to a service that the attacker benefits from in some way.
If the user is an administrator, then the risk increases significantly, as the admin user typically has elevated privileges. Imagine for example, maliciously inviting or promoting other collaborators / users with admin privileges (without the administrators consent).
Two factor and MFA already goes a long way to mitigate these risks, but users are often reluctant and not willing to go through the extra steps. Good MFA policies should be in place and enforced in your IT systems, especially for administrative accounts.
Common Attack Vectors
There are well know attack vectors used for successful CSRF exploitation, the common ones being:
- Login CSRF - Force (authenticated) user to execute request to website
- Stored CSRF - Chained with XSS, spreads to other users (amplifies severity)
Oftentimes, vulnerabilities get chained together (like in the case of stored CSRF), increasing their reach and severity significantly.
In the next section we will look into how these attack vectors can be chained together, and describe the tactics, techniques and procedures in more detail.
Tactics, Techniques and Procedures (TTP)
Generally speaking, this refers to the behavior of a malicious actor.
- Tactics refer to the high-level overview of the behavior.
- Techniques provide detailed descriptions of the behavior, relating to the tactic.
- Procedures are highly detailed descriptions of the technique.
This forms part of what is called Indicators of Compromise (IOC). They are used to do advanced threat detection. One good example of a framework that uses these IOC’s, is the Mitre ATT&CK framework.
Lets consider 3 use cases, where the first one is a pure CSRF exploit, then some examples that uses chained exploits to create an even more devastating attack vector.
Tactic: Social Engineering + URL hijacking
Technique:
- Building an exploit URL or script that has a CSRF vulnerability
- Trick users into clicking the URL using Social Engineering (eg: post on Social Media)
- URL opens in the browser of the target victim, sends request (validated as target user)
- (Optionally) Force user to log onto credential stealing clone of the original website
Procedure: T1566 (MITRE Attack Framework) - Phishing
Tactic: Using code injection (eg, chained with XSS)
Technique:
- Find way to inject unsanitized (HTML) input into a vulnerable website
- Build a malicious HTML tag, (eg: IMG that triggers code)
- Submit malicious input to the server, stored and rendered on subsequent page loads
- Wait for authenticated users to login, and trigger the malicious code
- Malicious requests submitted to the server (forged, from the victim user’s machine)
- (Optionally) Attempt account takeover by changing user’s email address / other details
Procedure: T1608 (MITRE Attack Framework) - Drive-by Target
Tactic: Watering hole attacks (eg, chained with XSS + CORS)
Technique:
- Goal is to expose/identify users of a targeted website (eg: track user activity)
- Same as the previous one (chained with XSS), except the last 2 steps.
- On page visit, send request to an attacker controlled website (eg: grab session + cookies)
- The attacker can then use the stolen information in later campaigns (eg: session highjacking)
Procedure: T1189 (MITRE Attack Framework) - Drive-by Compromise
Preventing CSRF attacks
From the business perspective, cyber security threats like CSRF should be taken very seriously, and business risks should be carefully reviewed and evaluated.
The amount of risk an organisation accepts to take, comes from the top, but they also need to be properly informed about the implications and risks, to make informed decisions.
From a technical perspective, a good place to start would be the OWASP CSRF Cheat Sheet, and for custom software development projects, there is also:
Use a Cyber Security Framework
Often its hard to know where to start, and how to quantify the risk. For this reason Cyber Security Frameworks were created, to help guide both governments and organisations to use standards and best practices to combat cyber crime.
I highly recommended using a cyber security framework, like NIST CSF to quantify and evaluate your security risks on a continuous basis.
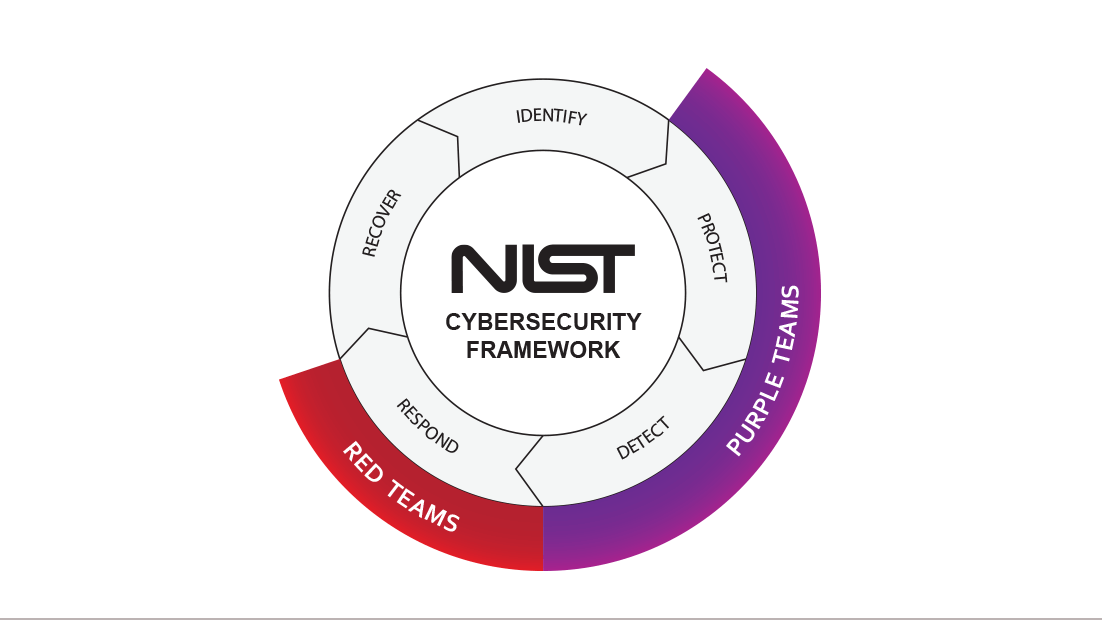
Its a simple process driven feedback loop, and works for organisations of any size.
- Identify the assets that bring business value (eg: customer facing servers on the internet)
- Protect assets that bring business value (eg: patch & update software and OS on servers)
- Detect intrusions and monitor indicators of compromise (eg: audit logs, events, SIEM)
- Respond to security incidents, prioritising most critical vulnerabilities detected, stop attacks.
- Recover your systems and infrastructure (eg: often involves a disaster recovery plan)
The last step (Recover) often feeds back into the first one (Identify), seeing that there is probably a great learning opportunity from an incident or attack, to better secure your assets in the future.
Summary and Conclusion
Cyber security vulnerabilities like Cross Site Request Forgery could leave severe impacts on your business or organisation, and can really hurt your bottom line (sales & profits).
Fortunately, there is a lot of well documented and open source information on procedures and playbooks for how to deal with these kinds of threats. The OWASP Top 10 is a good place to start.
A good security posture is also important, like adopting a Cyber Security Framework that will help you quantify and mitigate these kinds of security risks using a structured approach.
References
- Brief Explanation of Request-Response Model
- Wikipedia - Hyperlink
- Indicators of Compromise (IOC)
- What is Social Engineering
- Mitre ATT&CK framework
- GDPR (General Data Protection Regulation)
- PCI DSS (Payment Card Industry Data Security Standard)
- HIPPA (Health Insurance Portability and Accountability Act)
- NIST CSF (National Institute of Science and Technology)